
Your Trusted Source in CyberSecurity!
Get StartedVulnSniper
The Worlds First fully Automated Hacking Tool powered by Artificial Intelligence & Machine Learning integration!
Full Autonomous Penetration Testing
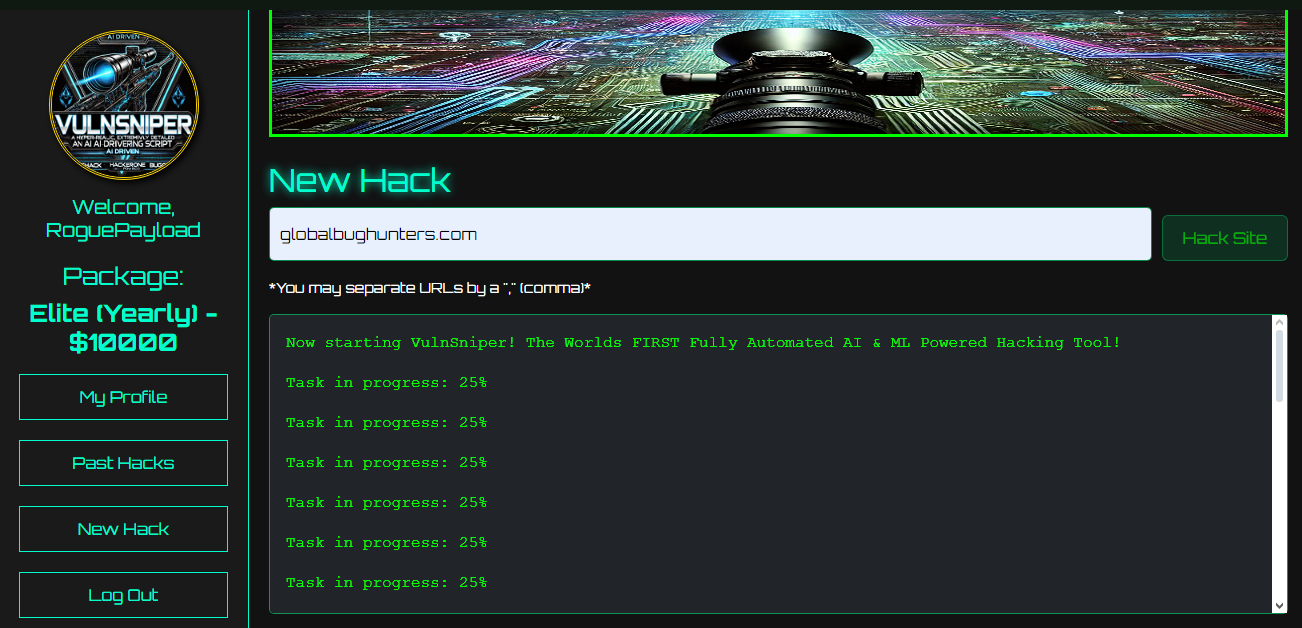
Now you can hack just like a real PRO! Fully automated Hacking operations built on Kali Linux Operating System!
Automated CVE Detection & Exploitation
Fully capable of discovering & exploiting a variety of CVE's including:
* API
* IDOR
* RSS
* XSS
* RCE
* SQLi
+ More to come soon!
Multiple Package Options
Select from a handful of different packages with different payment structures!
* Hacker ~ $1,000 Yearly | $100 Monthly
* Pro ~ $5,000 Yearly | $450 Monthly
* Elite ~ $10,000 Yearly | $1,000 Monthly
* Enterprise ~ $150,000 Yearly | $17,000 Monthly







Redefining Cybersecurity with Expertise and Innovation
At Global Bug Hunters, an AI-driven powerhouse dedicated to securing the digital landscape. With relentless focus, we provide unparalleled cybersecurity solutions tailored to safeguard your most critical assets.
-
Comprehensive Penetration Testing & Vulnerability Assessments
Our team of elite ethical hackers rigorously tests your web, mobile, and network environments, identifying vulnerabilities before attackers can exploit them.
-
AI-Driven Security Solutions
We harness cutting-edge AI technologies to provide real-time threat detection and automated protection, ensuring your infrastructure is fortified 24/7.
As pioneers in cybersecurity, we combine human expertise with advanced artificial intelligence to deliver scalable, future-proof security solutions. Trust Global Bug Hunters to protect your digital environment with unmatched rigor, innovation, and dedication to excellence.
Clients
Projects
Hours Of Support
Servers Launched
Our Services
At Global Bug Hunters, we provide cutting-edge cybersecurity, development, and hosting solutions designed to safeguard and optimize your digital infrastructure.
Penetration Testing
We conduct comprehensive penetration testing to uncover vulnerabilities in your digital infrastructure before attackers can exploit them.
Network Penetration Testing
Ensure the security of your network with rigorous testing that exposes weak points, providing actionable insights for network hardening.
Web Application Penetration Testing
We assess web applications for security gaps, ensuring your platforms are safe from external threats and meet industry compliance standards.
Mobile Application Penetration Testing
Protect your mobile apps from potential exploits with thorough testing tailored to both Android and iOS environments.
Threat Intelligence & Monitoring
Stay ahead of cyber threats with our real-time monitoring and intelligence services that detect and neutralize risks before they escalate.
Security Architecture Design & Implementation
We design and implement robust security architectures tailored to your organization's unique needs, ensuring full protection from the ground up.
Website Development Services
From basic informational sites to e-commerce platforms, we build high-performance, secure websites tailored to your business goals.
Advanced Web Application Development
We specialize in creating complex, scalable web applications that combine functionality, security, and user experience.
Android Application Development
Develop high-performance Android apps that are secure, user-friendly, and optimized for a wide range of devices.
iPhone Application Development
Our iPhone app development ensures sleek, secure, and feature-rich mobile experiences for your users, with seamless integration into the iOS ecosystem.
Web & Email Hosting Solutions
Reliable and secure hosting services for your web and email systems, ensuring optimal uptime and performance.
Web & Email Security Solutions
We implement advanced security protocols to safeguard your web and email communications from unauthorized access and cyber threats.
Test Your Cybersecurity Knowledge!
Can you spot the tricky answers and prove your expertise? Take the quiz and see if you can beat the challenge!
1. What does HTTP stand for?
Our Impact
Global Bug Hunters is at the forefront of cybersecurity and digital solutions, providing robust services that safeguard companies from the ever-evolving landscape of cyber threats. Here are some of our most impactful engagements:







Our Services
Explore the range of services we provide to meet your digital needs, from web development to advanced cybersecurity solutions. Contact us for tailored quotes and details.
Websites
Starting at $450
- Informational Websites
- E-Commerce Platforms
- Blog Websites
- Custom Web Applications
- Responsive Design & SEO Optimized
- API Integration & Usage
Mobile Apps
Starting at $4999
- Android App Development
- iPhone App Development
- Custom Features & Integrations
- App Store Optimization (ASO)
- Cross-Platform Compatibility
Penetration Testing
Starting at $1999
- Web Application Penetration Testing
- Network Penetration Testing
- Server Security Audits
- Physical Security Assessments
- Comprehensive Vulnerability Reporting
Hosting & Security
Custom Pricing
- Web & Email Hosting
- Domain Registration & Management
- Secure Data Transfer Services
- Email Security & Encryption
- 24/7 Support & Monitoring
- Custom Firewall Rules
Frequently Asked Questions
We answer your most pressing questions about cybersecurity, penetration testing, web and app development, and hosting & security solutions, ensuring you’re always ahead of the curve.
What’s the advantage of having a custom-built website over using templates?
A custom-built website is tailored specifically to your business needs, offering greater security, scalability, and flexibility. Unlike templates, which can be restrictive and vulnerable to common exploits, our custom development focuses on creating secure, optimized, and scalable platforms for your business, ensuring that your site is secure from the ground up.
Do you offer e-commerce solutions for websites?
Yes, we provide end-to-end e-commerce solutions that integrate secure payment gateways, SSL certificates, and advanced encryption protocols to ensure the safe transmission of sensitive data. We specialize in building secure, high-performance e-commerce platforms that can scale with your business while protecting your customers' data.
What’s the process for developing a mobile app?
Our mobile app development process begins with understanding your business goals and requirements. We then move to the design and development phases, focusing on security, performance, and user experience. We also conduct rigorous security testing before deployment, ensuring your app is resilient to exploits like data leakage, unauthorized access, and other threats.
How do you ensure the security of mobile apps?
We use the latest encryption techniques, including AES and SSL/TLS protocols, and implement multi-factor authentication (MFA) to secure your mobile applications. Additionally, we perform thorough penetration testing to identify and mitigate any vulnerabilities before deployment, ensuring your app meets industry standards like OWASP Mobile Top 10.
What kind of security do you offer for web and email hosting?
We offer end-to-end hosting solutions with built-in security features such as DDoS protection, firewall configurations, and automatic backups. For email hosting, we implement encryption protocols, spam filtering, and two-factor authentication (2FA) to ensure your communications remain private and secure. Our infrastructure is monitored 24/7 to detect and mitigate potential threats in real time.
Can you assist with migrating our current website and email to a more secure hosting environment?
Yes, we specialize in secure website and email migration. We ensure minimal downtime and no data loss during the transition, while configuring security protocols like HTTPS, SSL/TLS encryption, and DNSSEC to protect your domains from attacks such as DNS spoofing and man-in-the-middle attacks. After migration, we continue to monitor and optimize for security and performance.
What types of penetration testing do you provide?
We offer a comprehensive range of penetration testing services, including web application, network, server, and even physical security testing. Our team uses industry-leading methodologies, including OWASP for web apps and PTES (Penetration Testing Execution Standard) for network and infrastructure testing, to uncover vulnerabilities and simulate real-world attack scenarios.
Why is regular penetration testing important?
Regular penetration testing helps identify vulnerabilities in your systems before cybercriminals can exploit them. It ensures that your security controls are effective, up-to-date, and resilient against the latest attack vectors. By simulating real-world attacks, we can help you mitigate risks and meet compliance requirements like GDPR, HIPAA, or PCI-DSS.
How do you protect against data breaches and ransomware attacks?
We deploy a multi-layered approach to cybersecurity, incorporating threat detection, encryption, regular patching, and endpoint protection to safeguard your data from breaches and ransomware. Our proactive monitoring systems detect abnormal activity, and our incident response team is ready to address potential breaches immediately.
What steps do you take to secure sensitive data during storage and transmission?
We use advanced encryption standards (AES-256) for data at rest and TLS 1.3 for data in transit, ensuring maximum protection. We also implement role-based access controls (RBAC), data tokenization, and secure key management to protect your most sensitive data from unauthorized access or leaks.
